Applicable Products
- Citrix Gateway
Scenario: A Citrix Administrator is in the process of migrating a Citrix Virtual Apps and Desktops on-premises deployment to Citrix Cloud with an on-premises resource location. StoreFront and Citrix ADC machines are located on premises. The administrator notices that application enumeration is working, but application launch is failing with an. Architecture and introduction to Citrix Cloud please visit the Citrix Cloud page. Receiver Internet Firewall Citrix Cloud XenApp and XenDesktop Service StoreFront On premise Active Directory Hypervisors Server VDAs Desktop VDAs Cloud Connector NetScaler Gateway. Receiver is client side, it talks to storefront to aggregate applications. Storefront talks to delivery controllers to find out who has access to what apps, and then presents it in a web interface, or via a web service for receiver to consume Storefront is the replacement for the old web interface. Scenario: A Citrix Administrator is enabling TLS Secure connections between the Cloud Connectors and on-premises StoreFront. After configuring the TLS certificate on all Cloud Connectors and disabling HTTP connections, the administrator finds that no resources are being enumerated. Which extra step does the administrator need to take to allow enumeration to work between on-premises.
Objective
Instructions
To configure NetScaler Gateway on NetScaler products,below is the procedure to follow:1) On Microsoft Azure, we will configure a Network Interface for NetScaler Gateway with a public and a private IP.
2) Public IP assigned to above created interface will be resolvable to NetScaler gateway URL which we will configure later. Create a DNS A record on your DNS sever which points to public IP of NetScaler Gateway to its URL.

3) Gateway Configuration will be completed in following steps:
- If VPX is hosted on Azure then NetScaler does not have SNIP.
- Configure Virtual IP on NetScaler. Navigate to System -> Network -> IPs and add a IP for NetScaler Gateway VPN Server and select the IP type as Virtual IP.
- After configuring Virtual IP, configure NetScaler Gateway VPN server. Navigate to NetScaler Gateway > NetScaler Gateway Virtual Servers.
- Provide Name and IP address for virtual server and check ICA only check box and enable authentication check box as well.
- Bind server certificate to server and add STA server and click on Done.
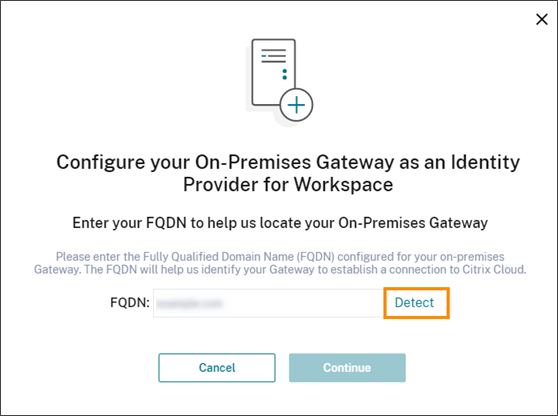
 4) Login to your Citrix Cloud account and click on XenApp and XenDesktop services. You will re-directed to another GUI with gateway configuration which will similar to
4) Login to your Citrix Cloud account and click on XenApp and XenDesktop services. You will re-directed to another GUI with gateway configuration which will similar to5) In above screenshot we are configuring our own NetScaler Gateway so we will use 'user your own NetScaler gateway in the resource location'. Here give URL for your NetScaler Gateway which will be resolvable to your NetScaler gateway URL.
For application/desktop launch, you have to access StoreFront URL not NetScaler Gateway. NetScaler Gateway is not doing any authentication here as it is acting as a proxy. Access the StoreFront URL on browser as:
Note: If you will check the downloaded ICA file, you will see SSL proxy host as NetScaler Gateway URL.
2.Under the 'Server Certificate' console, in the 'Action' section, click on “Create Certificate Request':
3. Fill in the information as shown in the 'Request Certificate' popup window, while reflecting your company details. For the “Common name” of the certificate, we can use wildcard. This will eliminate the need of creating individual certificate for each Citrix Cloud Connector. Note: Please, follow your company security guidance when deciding if the wildcard cert will be used.
4. Click next and change the “Bit length” to “2048”.
5. Specify the path and the name of the certificate request, and click 'Finish':
6. In Windows Explorer, navigate to the location from the previously saved certificate request, and open the text file in Notepad:
7. In a browser, preferably on same server where the IIS is used, navigate to the 'Certificate Authority Server' (http://yourserver/certsrv), and then click on 'Request a certificate':
Citrix Cloud On Premise Storefront Free
8. Select “Advanced certificate request” option, and then “Submit a certificate request by using a base 64-encoded CMC or PKCS #10 file”:9. Copy-paste the information from the Notepad that was opened in step #6. Make sure that at the end, the extra space is removed. In the “Certificate Template” drop-down menu, select “Web Server”, and click Submit:
10. After the certificate request, has been submitted, download page will be presented. Select “Base 64 encoded” and “Download certificate” is used.
11. To compete the certificate, navigate to the IIS and 'Server Certificates', and under the “Action” section, click on 'Complete Certificate Request':
12. In the new “Complete Certificate Request” popup windows, browse to the downloaded certificate file, give it “Friendly name” that will be recognizable:
13. In the IIS console the certificate name will appear as the Friendly name given in the previous step, and the certificate will be wild card certificate:
14. To export the certificate with the private key, open mmc console and add the “Certificates” snap-in for the local computer:
15. Previously we selected Personal store, and navigating to the store in the mmc we can locate the certificate:
16. To export the certificate and the private key, right click on the certificate and navigate to 'All tasks' and 'Export'. Click Next on the new 'Certificate Export' popup windows. On the next screen select 'Yes, export the private key', and click next:
17. Click next on the 'Export File Format' screen, without changing anything. That will open the Security screen where Password option should be selected, and password should be provided. Please remember this password, since it will be later used on the Citrix Cloud Connectors when importing the certificate. Click Next:
18. Select export location and give name to the certificate pfx file that will be exported. Click Next and Finish, to complete the export:
19. Move the certificate on the Cloud Connector, to import the certificate. Then double-click the certificate, and in the “Certificate Import Wizard”, select Local Machine:
20. Confirm that the 'Browse' is showing the correct pfx file, and click Next:
21. On 'Private key protection' window of the 'Certificate Import Wizard', enter the password from step 17. If there are plans on reusing the certificate, since it is wildcard certificate, make sure that checkbox next to 'Mark the key as exportable' is selected. Click next:
22. Select 'Place all certificates in the following store' and browsing to the 'Personal' store:
23. Click Next twice and Finish to complete the certificate import.
24. To confirm that the certificate has been properly installed, open mmc and add “Certificates” snap-in for local computer:
25. Navigate to the 'Personal' store and then 'Certificates'. The list of certificate should include the newly imported Cloud Connector certificate and the domain root certificate:
 26. The root certificate should be also part of the 'Trusted root certificates':
26. The root certificate should be also part of the 'Trusted root certificates':27. Next task will consist of registering the SSL certificate for HTTPS on the Cloud Connector. For Windows Server 2008 and onwards, there is a built-in utility called netsh which allows to make SSL certificate bindings to a specific port. For more information, refer to the – Microsoft MSDN article How to: Configure a Port with an SSL Certificate.
28. In elevated Command Prompt, following command will be run:
'C:>netsh> http add sslcert ipport=<IP address>:<Port Number> certhash=<Certificate Hash Number> appid={<Citrix Broker Service GUID>}'
2. If there is need Cloud Connector configuration with IPv4 and IPv6 addresses, then 0.0.0.0 can be used as the IP address in the netsh command. This makes the binding for all IP addresses on the Cloud Connector.
3. The Certificate Hash Number can be located in two places:
4. Make sure that Certificate Hash does not have spaces when entered in the netsh command.
5. To obtain the Citrix Broker Service GUID on the Cloud Connector, in the Registry Editor, select Find, and search for Citrix Broker Service. The search should return an entry in the following registry location HKEY_CLASSES_ROOTInstallerProducts.;

- If there are multiple Cloud Connectors used, and the certificate is not wild-card, please repeat all the steps for each Cloud Connector.
- If the wild-card certificate was used, repeat only steps 19 to 29.




